You can’t defend against threats you don’t address says Cisco. There are 44% of cyber security alerts that remain undiscovered, therefore businesses in Asia and across the globe are in crucial need of effective and surefire solutions.
The Cisco 2017 Annual Cyber security Report has been revealed to help organizations respond meritoriously against the constantly evolving and advanced cyber threats.
Malware malicious software is a software that is aimed to infiltrate and damage your computer, access sensitive and confidential information or steal your passwords. The types of malware include spyware, viruses, adware, phishing, ransomware, browser hijackers, Trojan horses, worms, and rootkits.
Malware usually enters your system via the Internet or an email, however, it can also use hacked websites, free subscriptions, music files, software, or anything else that is downloaded from the internet to penetrate into your computer or sometimes device.

Most Commonly Detected Malware
Security threats are a big nuisance. When you already have so much on your plate including sales, marketing, and customer satisfaction to take care of, it is really hard to find time for internet security. But, as we are digitalizing our processes, operations and all other practices, our workspaces are getting more prone to cyber-attacks.
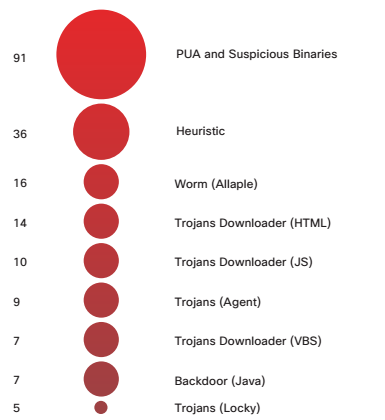
1 – Source: Cisco Security Research
Mentioned here are some of the most commonly detected malware you cannot afford to ignore:
1. Reconnaissance
Reconnaissance attacks are an attempt to extract useful and sensitive information about the victim systems, computers and networks. This attack serves as an initial step in the persuasion of other subsequent attacks that are intended to exploit the targeted computer. Reconnaissance attacks can either be active (involving port scans and OS scans) or passive (involving analysis of publicly available resources and host traffic to assess the victim’s vulnerabilities).
Symantec—a security firm – claims that it has observed a new Reconnaissance malware campaign that is targeting the energy sectors and trying to steal their confidential information, especially those of Middle East.

2. PUA and Suspicious Binaries
You might have seen some unwanted toolbars or browser extensions in your system before, they are because of PUA (potentially unwanted application) and Suspicious Windows binaries. These programs deliver threats like spyware and adware. At times, they run different processes in the background without letting you know about their presence and decelerate your PC.
PUA makes the computer slow and acts differently every time. It can access the rootkit codes to steal your financial information, and can eventually lead to monetary harms.
3. Facebook scams
Being used by around 1.8 monthly active users, Facebook serves as a breeding ground for cyber crime. The phishing attacks on Facebook are quite popular and are aimed to acquire your login credentials. Facebook has been recently working on eliminating fake news and hoaxes after the U.S. Elections 2017.
One of the most common examples of Facebook scams is that the Facebook are lured with click bait captions and heading that are apparently linked to interesting or a controversial news story. These links can actually direct you to dangerous waters.
4. Trojan Downloader
Trojan-Downloader installs itself to the victim computer and with the help of a working internet connection, it connects to a website or remote server to download other harmful programs, mostly malware onto the system that has been attacked.
Hackers also use malware that is accompanied by freeware downloads, and once you install them they can steal your password, and give the scammers the complete control of your system.
5. Browser redirection malware
When your browser get infected by malware, you are redirected to annoying, unwanted websites and malicious advertising a malvertising. This malware rarely contributes into serious permanent harm to the victim, as it is mostly used to promote ransomware and different malware campaigns.
This type of malware gathers the data about you or your office secrets and confidential files (when you are using an office computer or device) to exploit it afterwards.
6. Browser Redirection-Downloads
Besides redirecting the browser, some malware also automatically download the vicious malware to the victim computers and make them unprotected to the cyber-attacks. Many hackers use this malware to breach inside a company’s network to steal passwords that they can sell or use for executing intelligence gathering.
7. Phishing Links
Phishing is identity theft that is growing exponentially amongst cyber-terrorists. Phishing links and fake emails take you to deceitful web pages that apparently look legit, but are quite effective for hackers in stealing your personal and sensitive information,such as credit card information and passwords.
These links enable hackers to get your clients information from your office computers.This information further leads them to steal your client’s credit card details and bank account passwords, let alone the name of their kids, photographs, ages and every piece of personal details.
8. Android Trojans
Android Trojan is a malicious app that affects Android OS. It sabotages the security of Android devices or jeopardizes user’s privacy. Usually, this malware steals personal or payment information of the user, access different functions of the device using backdoor, sends inappropriate text messages, and sometimes encrypt the Android devices in order to harm the users financially. Loki malware is an example of Android Trojans.
Remember, no matter how small or big your business is, you should focus on making it secure against cyber scams. Assuming that your small office is not valuable to the scammers is a blunder, as your small business with no security practices makes them more vulnerable to cyber crimes.
What if you have been hit by any of these scams? You should reach your local authorities like, the Federal Trade Commission (FTC) or Internet Crime Complaint Centers as soon as possible to file your complaints against cyber crimes.
Author Bio:
David Harris is a logo designer at Logo Glaze where he is creates custom logo design. He is a graphic designer by profession but he is a writer in nature. He has an experience of more than a decade in the design and development industry and loves to help people achieve their dreams. You can follow him on his Twitter as well.






Be the first to comment on "8 Types of Malware You Cannot Afford to Ignore"