SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols developed by Netscape. They provide authentication and encryption capabilities between servers, applications, and machines for the secure exchange of data over a network. These two terms are often used interchangeably, but did you know that one is actually the predecessor of the other?
The security flaws with SSL 3.0 led to the creation of a better, more secure solution: TLS 1.0 – which is why it’s sometimes referred to as SSL 3.1. The use of TLS even translates into the VPN industry as popular protocols such as SSTP and OpenVPN rely on it for exchanging keys and certificate-based authentication.
SSL VPN is another software based on SSL that serves as a secure web browser. Unlike normal VPNs, it doesn’t require a pre-installed client and encrypts traffic between endpoints using SSL or TLS protocols rather than the standard IPSec (Internet Protocol Security). In this short guide, we’ll take a closer look at both SSL and TLS:
What is SSL?
Secure Sockets Layer, or SSL, is an encryption technology used to establish a secure link between a web server (website) and a browser (client), ensuring all the data passing through remains private. It’s used by many websites for safeguarding the online transactions of their customers. Ever visited a website with a pop up message telling you there was a problem with the SSL certificate of the web page?
That usually happens because a SSL certificate contain different pieces of information such as the company’s domain name, full name, address, city, country, and certificate expiration date. If these checks are unsuccessful, you’re displayed an error message by your browser which warns you that the website you want to connect to isn’t secure.
However, since SSL 3.0 is old and its components outdated, the protocol is now considered insecure and vulnerable to attacks such as POODLE. Therefore, it can’t be relied upon for protecting sensitive communication and is being replaced by TLS on websites across the world to provide adequate security from virtual threats.
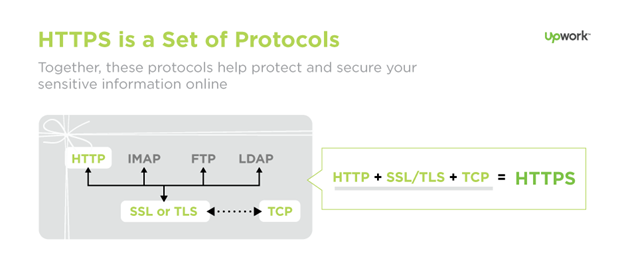
What is TLS?
Transport Layer Security, or TLS, is the successor of SSL 3.0, whose use has been denounced by the IETF (Internet Engineering Task Force), the main Internet standards body. The latest versions of TLS– like TLS 1.2 and 1.3 – are now significantly safer to use because majority of the previous security flaws have been eliminated. Since TLS 1.3 has just been released as of August 2018, widespread implementation is yet to come.
This makes TLS, when properly configured, more resilient to attacks as it provides stronger ciphers and encryption methods. In spite of this, there are many websites today that don’t use or support the newer versions of TLS, which means they’re still utilizing weaker encryption and ciphers – putting their customer’s information at risk!
SSL, TLS, and VPN
Many leading VPN providers have recognized the weaknesses of SSL 3.0 and TLS 1.0 and have updated their services with the latest TLS protection utilized by numerous protocols. TLS successfully prevents eavesdropping and alteration by providing data integrity between a VPN client and a VPN server.
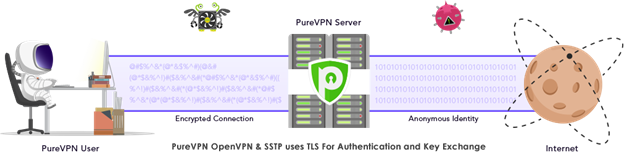
In SSL VPNs, TLS is used for enabling authenticated users to establish a secure remote-access connection. PureVPN offers both OpenVPN and SSTP VPN protocols, which implement TLS technology to encrypt data and prevent interested parties from sniffing the traffic over deep packet inspection.
Final Verdict: SSL vs TLS
You’re better off opting for the newer TLS 1.2/1.3 – because they’re faster and more secure than the previous version. If you want to configure a mail server or messaging application, TLS technology will keep hackers and eavesdroppers from invading your network.
Similarly, when choosing a VPN service for your needs, make sure they offer up-to-date protection. You wouldn’t want to use one offering weaker ciphers and security certificates. After all, the whole purpose of a using is a VPN is to increase your anonymity and security on the Internet!



Be the first to comment on "A Quick Guide to SSL and TLS Protocols"